The internet used to be pretty open but unfortunately there are now a huge amount of filters and blocks applied from every level. This has led obviously to a huge amount of tools and software designed to bypass these filters primarily based on a core of proxy and VPN servers. But they can get expensive if you want any flexibility purely because you often need more in different countries. Think of my friend who is from Krakow originally but now lives in the UK – he often likes to connect back to websites in his home land for obvious reasons. But increasingly he will get blocked because of his location. What he needs is a Polish proxy in order to access these sites – for instance the Polish media channels.
But my friend also likes to watch some strange American series which is only available in the US, plus he likes a show on Canadian pilots on Canadian TV. So to watch all these he’d need a Polish, US and Canadian proxy or VPN service. You’ll notice that many of the proxy providers will sell you access to specific servers but they usually charge extra for each location. But there are a couple who just charge a single subscription and give you access to their entire network.
Here’s how one of my favorites works – first I connect to Google with my normal address.
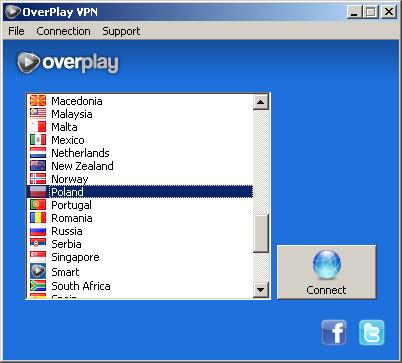
But unfortunately this means I am tied into a UK location, which is fine if you just want to access UK related sites but what if you want to access sites that are restricted to Poland, Russia, USA or anywhere else on the planet? I need to be able to fool these sites that I am located somewhere else which I can do through using either a proxy or VPN server. For this demonstration I am going to use a Poland based proxy from a company called Overplay.
Here’s what I do – just connect up to my Overplay software and scroll down their list of available proxies. From the screenshot you can see I have a polish proxy server available so I just connect through that. It takes about 10 seconds to connect and to extablish the connection after you put in your username and password.
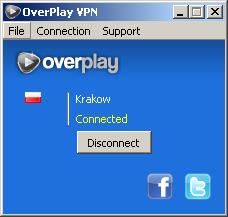
Then you’re connected – at this point you have a VPN tunnel connected between you and the Overplay server in Krakow, Poland. In plain English this means that you will now appear to every web site you visit to be from Poland. For instance here’s what you see if you visit Google whilst using the Poland proxy. The geo location checks your IP address and delivers the Polish version of the search engine.
Of course this isn’t particularly useful if you aren’t actually in Poland. However if you are getting blocked from a specific site because of your location it can be an incredibly useful tool. It means all Polish content is available to you whilst connected, any look ups will reveal your location to be Krakow because that’s where the server is located.